| Главная » Статьи » Мои статьи |
Wi-Fi network is available almost everywhere. Invisible threads of wireless channels entangled cities and villages, villas and houses, garages and offices. Despite the seeming security, there are always a few people, employees of the dark side of IT, which somehow bypass all these your defense mechanisms, and boldly go into your own private wireless, feeling right at home. For many ordinary users, this technology still remains a mystery, passed on from one generation of hackers to another. In the vast expanses of the Internet you can find dozens of articles and thousands of video instructions on how to hack Wi-Fi, sufferers are encouraged to view the training video, the matching password “qwerty123”, but, as a rule, a full guide of what is called “from-to” on this topic I have not yet met. What I actually decided to fill. Let's try to understand who, and why? 1. For some, it's a free Internet. It can be neighbors or travelers who don't want to pay 5 euros for the Internet, if they can try to use free of charge. 2. Someone tries to get your data by intercepting network traffic and then hacking your accounts. 3. It can be industrial espionage. I think that comment is not needed here. 4. Pentester testing network penetration, or simply hone their skills.
At the dawn of wireless access in the distant 1997, British scientists, as it is not too encumbered with security issues, believing that a 40-bit WEP encryption with a static key is more than enough. But malicious hackers on a couple of talented mathematicians, quickly figured out what was happening, and the network is protected even long WEP key in the whole of 104 bits soon became somehow amount to open. However, with the development of computer literacy among ordinary users, to find the WEP network now has become almost more difficult than open, therefore, the main attention will be paid to more frequent WPA/WPA2. Basic fallacy users - “I use WPA2, its not a hack”.
Of course developers WPA took into account the bitter experience of the implementation of WEP and filled the authorization procedure different steep dynamic algorithms that prevent ordinary hacker to quickly read the password over the air. In particular, over the air from the laptop (or whatever) to the access point is transmitted is certainly not the password itself, and some digital porridge handshake - handshake”, the resulting chewing long random number, password and network name (ESSID) with a pair of computationally complex iterative algorithms PBKDF2 and HMAC (particularly distinguished PBKDF2, which consists in the sequential organization of four thousand a hash transformation on the combination of the password+ESSID). Obviously, the main goal of the developers WPA was as much as possible to make life hackers and to exclude the possibility of rapid guessing a password by brute force, because it will have to calculate PBKDF2/HMAC-convolution for each version of the password, which, given the computational complexity of these algorithms and the number of possible combinations of characters in the password (and, i.e., the characters, the WPA password can be from 8 to 63), will last exactly until the next big Bang, or even longer. However, considering the love inexperienced users to the password “12345678” in the case of WPA-PSK (with WPA2-PSK, see above) it is quite possible the so-called dictionary attack, which is the brute force prepared the most common of several billion passwords, and if PBKDF2/HMAC convolution with one of them will give exactly the same answer as in caught handshakes - bingo! a password from us.
Well, having saved some hefty baggage of theoretical knowledge will move on to practical exercises. To do this, first define what we need from the hardware and what software is the most “iron” should be loaded. To intercept handshake will fit even the dead netbook. All that is required of him - a free USB port to connect the “right” Wi-Fi adapter (you can of course catch and built-in, but this is only if you attack a neighbor at Dorm, because the bandwidth of the signal built-in adapter and its strange antenna is unlikely to break at least one normal concrete wall, not to mention the couple hundred meters to the victim, which is very desirable to withstand not to Palitsa . A very good advantage of the netbook can be a light weight (if you have to run away) and the ability to work for a long time on battery. For solving the problem of guessing a password processing power of a netbook and a full laptop) won't be enough, but we will talk about it later, now we must focus on handshakes and methods of capture. Just above I mentioned the “correct” Wi-Fi adapter. What's it like is “correct”? First of all he must have an external antenna with a gain of at least 3 dBi, better 5-7 dBi connected through connector (this will allow for the need to connect instead of the standard pin external directional antenna and thus greatly increase the slaughter distance to the victim), the output signal power adapter should be at least 500 mW (27 dBm which is the same). Much to chase the power adapter is not worth, as the success of interception of handshakes depends not only on how loud we shout into the ether, but also how well hear the response of the victim, and this is usually a regular laptop (or even worse - smartphone) with all faults, its built-in Wi-Fi. Among wardrivers all generations the most “correct” are adapters Taiwanese company ALPHA Network, for example AWUS036H or similar. In addition to the alpha quite efficient products TP-LINK, for example TL-WN7200ND, although it costs twice cheaper compared to alpha, and thousands of models of other manufacturers similar to each other as two drops of water, good waitinig chipsets in nature, there is not so much.
As for software, it is generally used LINUX distributions. For example BackTrack or KALI LINUX
It should be noted that most things in Linux that runs in the terminal window. For example, what would we determine our network adapter, run the following command:
root@d1GGer:~# ifconfig
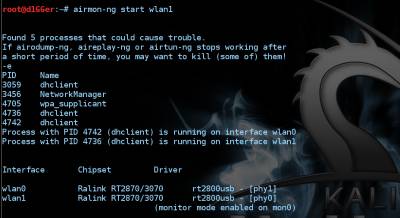
Our adapters are visible as wlan0 and wlan1. Now, translate, for example wlan1 mode Managed mode Monitor by running the following command:
root@d1GGer:~# airmon-ng start wlan1 After you run the command, you should see the following
Now, let's listen. It is very simple. Simply issue the following command:
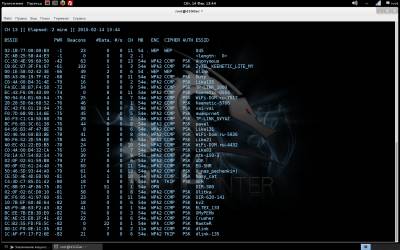
root@d1GGer:~# airodump-ng mon0 After running the command, you will see the following. The number of "points", depending on the power of your adapter.
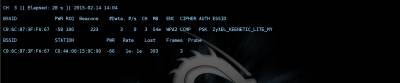
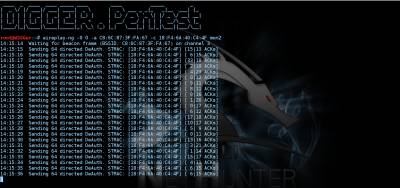
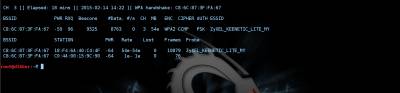
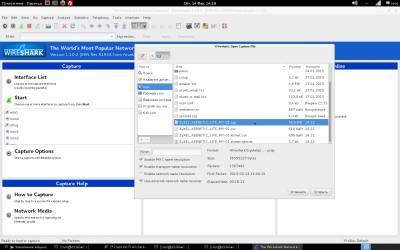
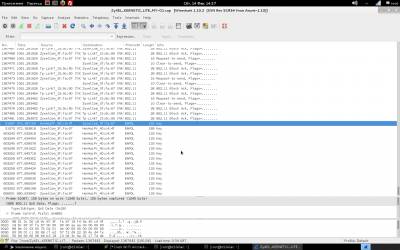
In the upper left corner can be seen as scanned channels (if you want to lock the channel, you need to call airodump-ng with the key-channel <channel numbers separated by commas>), followed by the table of found networks with showing (left to right): BSSID (MAC address of the network), the level of signal strength in dBm (depends on the receiver sensitivity, good adapters -80 dBm this is quite normal), the number of received Beacon frames are broadcast packets that carry information about the network), the number of received data packets and the reception rate (packets per second)the channel which broadcasts the access point, the point velocity access in megabits, the authentication type (OPN - open network, WEP, WPA, WPA2, encryption type, magic letters PSK with WPA/WPA2 (described above in the main 2) and, finally, the name of the network, i.e. its ESSID. Just below the main table is a table of current associations to the point. Looking ahead, I note that it is also important because it is possible to determine the activity and the MAC address of the clients for their subsequent deassociate. From the pictures above that we should have something to catch there and access points, and clients with good signal. It remains to choose a victim (so that the file is not much swell, you can record packets only from one access point having a key-bssid <MAC-address> or by limiting the channels as described just above) and give the command to write the packets to a file when the call key-w <prefix file name>. Important: if you have booted from the DVD file entry packages must conduct on an external flash drive or hard drive, pre-promontional their mount command: Once we have identified the victim, enter the following command: airodump-ng mon0 --channel № --bssid 00:00:00:00:00:00 -w /root/name Now you can pour a Cup of coffee and chew the sandwich waiting for the next client does not wish to cling to the access point and give us the coveted handshakes. By the way, after receiving handshakes in the top right corner, a warning will appear: WPA handshake: A0:21:B7:A0:71:3C. All done, and you can proceed to the next Chapter. When eaten all the sandwiches, and coffee is no longer climbs and handshakes all no, no, come bright idea that it would be nice to speed up the client with handshakes. For this part of the package aircrack-ng is a special utility that allows you to send the client requests deassociate (detach) from the access point, after which the client will again want to connect, and this is exactly what we expect. The utility is called aireplay-ng and run it in a separate window in parallel with the start airodump-ng to simultaneously record the results of your work. Run deassociation: aireplay-ng –deauth 0 0 -a 00:00:00:00:00:00 -c 11:11:11:11:11:11 wlan0 where it is obvious that we have an unlimited number of sessions the client deassociate 00:00:00:00:00:00 from the access point with BSSID 00:00:00:00:00:00 (the address of the client we took from the bottom of the table associations airodump-ng, it is not set, then deassociate will be broadcast query that is not as efficient as we would like. After carrying out this procedure (and nothing prevents us repeat it once more just in case) the probability to catch handshakes increases significantly. What a giant of the work done, we have *.cap-files" containing handshake and we can move on to the next step. But let's see what we caught and evaluate the quality of handshakes. For this purpose, we will use the WIRESHARK utility. Start the program. Then, open the file, and choose file, with permission .cap, as shown. Then, filter by PROTOCOL, and make sure that you have a content KEY To perform the following actions will be required: 1. aircrack-ng 2. File resolution .cap 3. Dictionary, brute force and dictionary. That would accomplish the following, the last step, enter the following command:
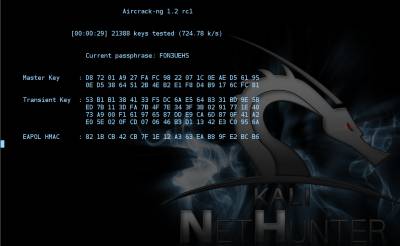
root@d1GGer:~# aircrack-ng /root/ZyXEL_KEENETIC_LITE_MY-01.cap -w /root/D1GGER/Pentest/Dictionarie/Bigpass.txt
As I hope you could understand this command, we ran aircrack-ng, and pointed out the path .cap file and the dictionary file. Well, then, begins the process of recovering passwords. Time to break the password depends on its complexity, whether you have a large number of options for passwords, and good luck. It may be several hours or perhaps several days. In parallel, you can run many processes of search, with different dictionaries. Everything depends only on the power of your iron.
How can you reduce the risks of hacking your network? Well, firstly, it is the creation of a strong password. Secondly, keeping your equipment up to date by installing all updates firmware. Configuring the settings for the identification and control of network users. In this, perhaps all. Take care of yourself, and remember:
BIG BROTHER iS WATCHING YOU!
www.youtube.com/c/+MegaD1gger
| |
| Просмотров: 2356 | | |
| Всего комментариев: 0 | |