| Главная » Статьи » Мои статьи |
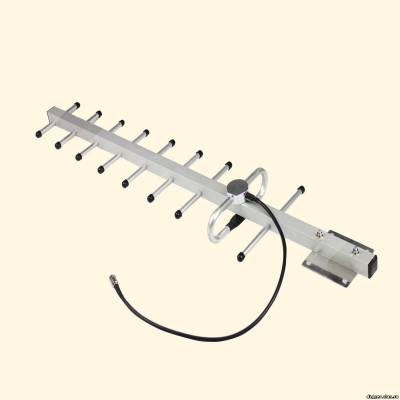
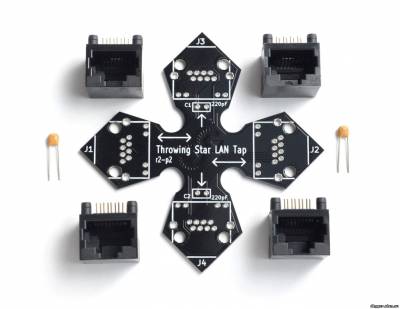
Unusual kinds of devices and gadgets is not only among the security officers and agents 007. Many devices have been specifically designed for the needs of hackers and security researchers. What are they? We will now discuss. Everyone who is seriously engaged in the pentest or hacking, for sure at least once in conditions, when for a successful attack lacked literally one step. In the book Kevin Mitnick's "The Art of Intrusion" describes in detail the story of one pantecta in which the obstacle was provided to the reviewer properly configured by the system administrator firewall. It would seem that the internal network of the company to penetrate no chance. But one of the team members found working at reception connector for connection to the mains and invisibly connected to it a miniature device for wireless access (which no one noticed until the end of the test). Thus a team of penetration testers has been granted direct access to the internal network through Wi-Fi. This is one of many examples illustrating to underestimate the hack device is not worth it. That is why today we consider the most interesting options that can be purchased online. So let's begin. The first tool is the WiFi Pineapple Mark IV. thirst of free Internet leads to the fact that people, arriving in some place or, say, the airport immediately start to check if there was a free Internet? Very few people know that under the guise of a public hotspot can act specially configured router, which intercepts the entire outdoor traffic (it's easy, still "goes" through it) and uses different kinds of MITM attacks to intercept data that is transmitted over a secure connection. For greater success, an attacker could exploit the sonorous name of the network like "wifi Guest" or even masquerading as popular providers, then hanging up on customers will not. Fake hot-spot (Rogue AP) is raised quite easily on any laptop. However, in the hacker community long known for attention to detail a device that implements the attack in the truest sense of the word from the box. Wi-Fi Pineapple, which appeared in 2008, now sold in its fourth modification. The first audit of the devices was for a joke disguised as a pineapple — hence the name of the device. In fact, it is a regular wireless router (based on a wireless chip Atheros AR9331 SoC and processor 400 MHz), but with the special, based on the OpenWRT firmware, which is enabled by default utilities such as Karma, DNS Spoof, SSL Strip, URL Snarf, ngrep, and others. Thus, it helps to turn on the device, configure the Internet (all configurable via the web interface) — and intercept user data. The router needs power supply, and it interferes with his mobility; however, there are plenty of options (which is being actively discussed on the official forum) is to use the batteries — so-called Battery Pack. They give the device two to three hours of Autonomous operation. The cost of this davisw varies from $99,99 The second tool, which we will tell - Ubertooth One. Unlike eavesdropping on Wi-Fi, which is easily arranged from a laptop with an appropriate wireless adapter, the Bluetooth analysis of the ether — a task much more complex. Or rather, was difficult before the show Michael Osman at the conference ShmooCon 2011 (video report youtu.be/KSd_1FE6z4Y), where he presented his project Ubertooth. Check out the difference. Industrial iron for BT-ether can be purchased for amounts starting from $ 10 000. Michael told how to collect a suitable device, costing less than a hundred bucks. In fact, it is a USB dongle with external antenna, built on the ARM Cortex-M3 processor. The adapter is originally designed to be translated in a promiscuous mode in which it is possible to passively intercept data from a Bluetooth broadcast, transmitted between other devices. This is an important option because most dongles pay attention only to what is addressed to them, ignoring everything else, and to affect such behavior impossible. In the case of Ubertooth One can intercept frames from Bluetooth-ether, and to use the usual utilities like Kismet. The device can be assembled by yourself, if your hands grow from the right place, or buy ready-to-use device in one of the authorized shops. The cost of this tool is $ 200 And of course, how can we ignore such a device, like a USB adapter. We will focus on the most common ALFA USB WiFi AWUS036NHA. If we talk about auditing wireless networks, for the implementation of the most frequent attacks and, in fact, the only obstacle becomes unsuitable Wi-Fi module built into the laptop. Unfortunately, manufacturers are not thinking about choosing the right chip, which, for example, supports the injection of arbitrary broadcast frames :). However, often no more than a mediocre innings — just to pull the data out of the ether. If you dig on the forums, you will find lots of recommendations about which adapter is best suited for wardriving. One of the options — ALFA USB WiFi AWUS036NHA. This Wi-Fi USB adapter high, Alfa AWUS036NHA power, built on the Atheros AR9271 chipset and working in the standards b/g/n (150 Mbps). It without superfluous dances with a tambourine can be used in major operating systems, including scriptkids-the BackTrack 5 distribution, which already contains all the necessary tools for wardriving. By the way, an external USB adapter to work in a familiar Windows, to use all the features on the guest (same Backtrack) running under a virtual machine with prosrochennym primary OS from USB port. The adapter is compatible with the Pineapple Mark IV. Starting with firmware version 2.2.0 Pineapple can be used for so-called deauth attacks. The essence of the attack is quite simple: customers are sent deauthentication frames, forcing them to re-connect. The attacker intercepts handshake'and WPA, which are then used to brute force WPA-key. The cost of the adapter is around $40 Reaver Pro. As you know, a long passphrase is to connect to a wireless WPA network reduces the likelihood of brute force. However, the complexity of implementation of this attack evaporates, if the wireless network supports WPS. About vulnerabilities in the technology we described in detail in ][032012, including its operation using the Reaver. The author of this tool has released a special kit that allows you to implement this attack. It consists of a wireless module and a bootable flash drive with pre-configured distribution. The goal of the attack is to find the WPS pin once it is received, the wireless point will provide us with your WPA key. Thus, as you can see, the length and complexity of key does not affect the duration of the attack. On average Reaver'have required from 4 to 10 hours for the selection of WPS-pin and. Honestly, when I first read that there is a hardware implementation of this attack, we imagine a small portable device that can be discreetly hidden in the reception zone for the desired access point. Indeed, in contrast to brute force a WPA key, which can be done anywhere (just enough to intercept the handshake), the attack is on WPS is active. That is, you need to be in the vicinity of the access point: if the reception will be insufficiently reliable, then bust a quick stop. A good alternative to Reaver Pro can be implemented by a software module for the WiFi Pineapple Mark IV (and a serious set of batteries to power it). While all that suggests the Creator of Reaver Pro is the ability to suspend the attack, so the next time to continue the interrupted place. The cost of this instrument $ 100 All wireless devices have a serious drawback — limited range. Reliable reception is often a key parameter for the successful implementation of the attack. The closer you sit to the goal together with your "strange" boxes-devices — the more attention you will attract more suspicion and cause. The further away from goal so it's safer and less noticeable. There are omnidirectional (also called omni), and a highly directional antenna. For example, we took the representative of the second type — 16dBi Yagi Antenna. This highly directional antenna allows you to be at a sufficient distance from the wireless network and to maintain the necessary level of signal. The connector RP-SMA it can be connected to the adapter, ALFA AWUS036H, "the box" WiFi Pineapple, Ubertooth One dongle, as well as to many other Wi-Fi devices. It is important to understand that this is only one of thousands of different antennas. The Network is not only sold a huge number of different antennas with varying performance characteristics, but also is a lot of instructions on how to quickly cobble together an antenna from scrap materials (for example, from banks or wire). The price is $30 USB Rubber Ducky - like the same without him. USB Rubber Ducky is analogous to the Teensy. The heart of the device is of 60 mega Hertz range 32-bit AVR microcontroller AT32UC3B1256, however, hardcoding something at a low level is not required. The device supports a surprisingly simple scripting language Duckyscript (similar to a conventional bat script), which is also already implemented various payload. To run the application, create Wi-Fi backdoor, to open a reverse shell, you can do everything the same as if you had physical access to the computer. More flexibility provides additional storage in form of microSD card, which can simultaneously accommodate multiple payloads. The functionality can be expanded through plug-in libraries, all the more so since the firmware is written in pure C, fully open and hosted on github. The chip is very small, but in order to make its use completely invisible, the developers offer a special casing from the stick. The cost of the device $ 70 Following the hack, the device is also provided that the attacker has access to: the truth, not to a specific computer and LAN cables. And he needed to passive and unnoticeable monitoring a network segment. The point is that it is impossible to detect programmatically — in fact, it is just a piece of cable that gives no. How is that possible? Throwing Star LAN Tap looks like a small chip in cruciform shape, at the ends which are four Ethernet ports. Imagine that we need to intercept traffic between two hosts (A and b) connected by cable. To do this, just cut the cable anywhere, and join the resulting gap through the Throwing Star LAN Tap. It is necessary to connect the gap through the ports J1 and J2, while J3 and J4 are used for monitoring. Here it should be noted that J3 and J4 are connected only to the cores responsible for getting the data is deliberately made in order monitorama machine to send a packet to the destination network (which will give the fact of monitoring). Throwing Star LAN Tap is designed to monitor the 10BaseT and 100BaseTX networks and does not require the power supplies. Due to the fact that the device doesn't use any power, it cannot monitor the network 1000BaseT. In this case, he has to reduce the quality, causing the machine to communicate at a lower speed (usually the speed of 100BASETX), which can passively monitor. The device is easy to solder yourself, all circuits are open (the concept of Open Source hardware). The cost of the device $ 15 GSM/GPS/Wi-Fi jammers. Talking about hacking devices, we could not avoid this class of devices, as jammer's or, in simple terms, jammers. We deliberately did not single out any individual device, and decided to look at a whole class of such devices. All of them, regardless of the technology that you want to silence, are based on the same principle — the debris air. It works out the same for mobile networks (GSM), where the phone communicates with a base station, or, for example, a GPS receiver, to determine the coordinates have to keep a connection with several satellites. The devices differ in range, power, size and General appearance. Suppressors of signal can be stationary (large bandura with antennas) or mobile, as, for example, under a pack of cigarettes. Online you can find a huge number of jammers, especially if you look at Chinese online shops. Now raging arguments about whether the legal use of such jammers in Russia. Last year was seriously proposed to use in schools when it was revealed (what a surprise!), despite all prohibitions, the students still carried by the cell phones during the unified state exam. It costs $100 The last few years, one of the essential attributes of each office worker has become a plastic card that allows you to open door locks of offices and premises. We are talking about the cards Mifare Classic 1K. The card is a plastic card which is placed inside the chip (chip), with protected memory, the receiver, transmitter and antenna. The memory of this card is 0.5, 1 or 4 KB and all the memory is divided into 16 sectors. Each sector consists of four blocks (three information and one to store the keys). The minimum data retention in the memory card Mifare is 10 years, and the number of write cycles about 100 000. These cards are passive storage devices, that is, to work and contactless data transmission energy and no battery is needed. The distance to the reader, which starts the data transfer is determined by the transmitter power of the reader and receiver sensitivity maps. If you need to copy this map or just to see what is written there, at your disposal there are different kinds of devices. It's so convenient: cards, often, break or get lost :). The most popular device for these ploys — http://www.thaieasyelec.com/en/ cost only $ 65. Attached are some copies of cards which can produce a clone that will allow you to plunge into the world of social engineering hacking methods. By the way, transport companies engaged in passenger transportation, very often uses the Mifare Ultralight. In addition, there are countless other devices to work with less popular clients in wireless communication networks, such as NFC, ZigBee and many others. NFC, by the way, is a logical continuation of a family of RFID, to work with even with the help of advanced mobile devices. The KeyGrabber. There are a huge number of commercial implementations of the ideas, including the KeyGrabber series, offering models for both PS/2 and USB keyboards. The manufacturer thought about how to make use of such devices more invisible. It is not enough, you need to connect to a Keylogger, it is necessary to periodically remove data from it. It turned out that the last can be simplified if the sniffer is to provide Wi-Fi adapter that can seamlessly connect to the closest access point and to send captured data to the e-mail. This same manufacturer also offers several other useful solutions. In addition to ready devices that looks like the adapter, you can buy KeyGrabber Module — ready chip that can be embedded in the PS/2 or USB keyboard. Also on sale are the device VideoGhost — "perehodnik" that plugs in between the monitor and the computer every ten seconds saves the screenshots to the built-in memory (2 GB). There are versions for DVI-, HDMI-, VGA-connectors, the price is starting at 149,99 dollar. The situation when access to the corporate network have to get through the skills of social engineering and special devices, are encountered in practice quite often. MiniPwner is a device, which in the case unnoticeable connection to the target network provides the attacker/pentester remote access to the network. The device is designed by engineer from Wisconsin, Kevin Bong, who collected the first prototype of a miniature spyware computer in a box from under candies. The gadget is designed to connect to a local network and the rapid collection of information. Immediately after connecting the computer establishes a SSH tunnel and opens the login from the outside. If you look inside, it is a regular router TP-Link TL-WR703N, has a memory of 4 GB and having wireless interface that supports 802.11 n and Gigabit Ethernet port. As firmware using a modified version of OpenWrt, which is pre-installed a lot of utilities necessary for the conduct of intelligence activities: Nmap, Tcpdump, Netcat, aircrack, and kismet, perl, openvpn, dsniff, nbtscan, snort, samba2-client elinks yafc, openssh-sftp-client and others. Autonomous operation, which is crucial for real-world use, provides a battery capacity of 1700 mAh, which is enough for five hours of intensive work, even if you enable the wireless LAN mode. So by connecting this device to the studied network, the researcher can get enough time to gain a foothold in it. It costs $100 Pwn Plug. As discussed above MiniPwner, Pwn Plug belongs to the class of so-called drop-box devices — i.e. devices that are invisible when you connect to the target network to provide remote access to the attacker/pentester. Outwardly the device is similar to the power adapter plug into the socket. For greater secrecy, the developers provide special stickers, masking Pwn Plug under air fresheners and similar household appliances. In fact, it's a full-fledged computer, running Debian 6, which, despite its small size, the eyeballs stuffed with a variety of devices and hacking software. Let's examine the Elite version — it is more "charged". So, this "freshener" is provided with three adapters: 3G, Wireless and USB Ethernet. Supports external SSH access over 3G/GSM cellular network. Has such an interesting story as Text-to-Bash: you can execute commands on the console by sending SMS messages. Supports HTTP proxies, SSH-VPN and OpenVPN. A rich set of hacker tools includes Metasploit, SET, Fast-Track, w3af, Kismet, Aircrack, SSLstrip, nmap, Hydra, dsniff, Scapy, Ettercap, tools for working with Bluetooth/VoIP/IPv6 and so on. As additional storage is used 16-Gigabyte SDHC card. Wireless version does not have 3G and USB Ethernet and, accordingly, may not boast of the support of remote access via the cellular network. Otherwise both versions identical. In General, the device is really cool, but the price tag is, quite frankly, bites $595. AR.Drone - This device is very different from all the others. After all, it can be... no, not to intercept the traffic, not to catch the keystrokes and save screenshots of your desktop — it can help you... to peek. Yes. Modern pentesting more and more like espionage, so experts do not neglect this opportunity. Frankly, seeing the AR.Drone in the store, I wouldn't have thought about the tests on the penetration or hacking. It is a toy of pure water: ordinary quadrocopter with a camera attached to it. The second version of the AR.Drone is equipped with high resolution camera, so, as it sounded fantastic and reminded espionage action, you can peek through the window, what's going on in the room, what equipment used, how employees behave. And not necessarily have a sharp eye and photographic memory: the camera you can attach the USB flash drive, which will be recorded videos. To control the device as easy as a remote you can use iPhone, iPad and Android, pre-installing a special application. The device can be used for peaceful purposes, making stunning pictures with the bird's eye view. So, even if the voyeurism is not for anyone with such a device still not bored. If you want to save, then you can build such a device samostojatelnosti, I recommend you explore the following resources:bit.ly/GVCflk — a post on habré, describing in some detail the process of creating a simple quadrocopter; bit.ly/o8pLgk — English site dedicated to the construction of the quadrocopter; bit.ly/fhWsjo resource on how to make robots, also contains articles about quadcopters. Completes our review of the device named Raspberry Pi, around which now a lot of noise. This is a simple single-Board computer developed by Raspberry Pi Foundation. The circuit is implemented with a processor ARM 11 with a clock frequency of 700 MHz and comparable to a credit / debit card. One of the advantages of this "computer" — it goes without housing, just in the form of chips, and it allows you to disguise it under almost anything. On the Board are ports of input/output, two USB 2.0 slots, compartment for memory cards SD/MMC/SDIO, Ethernet controller, composite and HDMI video outputs. As you can see, ideal for creating your budget drop-box and. In General, such a device with a good processor, low power consumption, connectivity Wi-Fi adapter via USB and your Linux on Board is a sin not to use for hidden installation. As the OS you can use any Linux distribution — Debian, Fedora, Ubuntu, but better specialized дистрибутивPwnPi issued by the craftsmen specifically for installation on the Raspberry Pi. It already contains all necessary hacking tools. Besides craftsmen eager to share their experience of installing it on a hidden server to the anonymous network I2P, install Metasploit, create a hardware sniffer, and more. Today is all. A review is made on materials of magazine "HACKER".
| |
| Просмотров: 1778 | | |
| Всего комментариев: 0 | |