| Главная » Статьи » Мои статьи |
Hacking Wi-Fi (part three)
The most popular topic is how to hack Wi-Fi network. In this, the next review, we will consider another way of attacks on wireless networks, with the aim of obtaining access to the latter. This way, not much different from what we saw in the previous article. As in the previous case, in this technique, attack, use tools such as : REAVER, and Python script. The difference of this method is that it is more visualized. Well, let's start.
Procedure as in the previous cases, in General the same. Define the interface of our network card, by running the command airmon-ng. Next, we'll move our network card or adapter in monitor mode using the command airmon-ng start wlan(?)
Now, we need the script to download which you can get in there. After you have downloaded the archive, it is necessary to unpack. The archive was downloaded to the desktop, run the following commands: root@d1GGer:~# cd Desktop To extract the contents of the archive, write the command:
root@d1GGer:~/Desktop# unzip WPSPIN.zip Team ls look what he learned from . Now, we need to navigate to the directory WPSPIN for this type the command: root@d1GGer:~/Desktop# cd WPSPIN And at the final stage before we entered two teams:
root@d1GGer:~/Desktop/WPSPIN# chmod 777 WPSPIN.sh
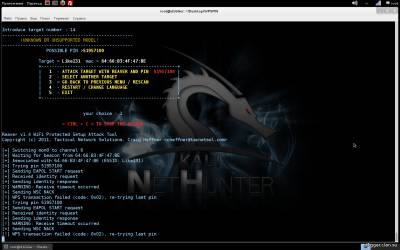
root@d1GGer:~/Desktop/WPSPIN# ./WPSPIN.sh After you have completed all the commands, you will see the following window
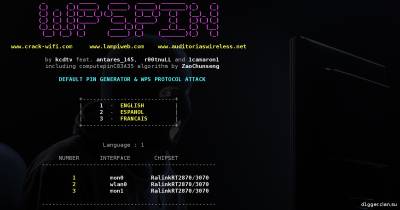
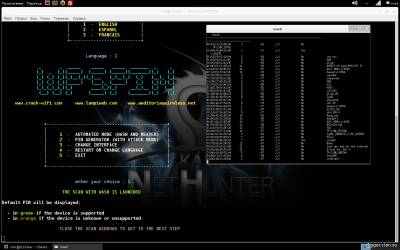
Further, as you might guess, you must choose the language of the program, and choose the method of attack. We will consider the first method. After selection, utility wash, which will scan range, for networks with WPS enabled.
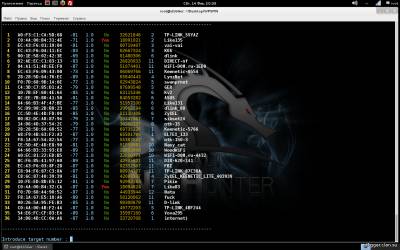
Once you have decided that it is enough to scan the range, just click on the small cross window. All scanned network, will appear in the large window.
Further, as in the previous case, everything is intuitive. You must choose the network that you will be attacked by specifying its sequence number, and specify the type of attack. After that, the program will start to do everything by myself, and you will again pour coffee and wait.
If the attack is successful, when scanning is finished, you will see results that will contain the password to the victim's wireless network
| |
| Просмотров: 996 | |
| Всего комментариев: 0 | |