| Главная » Статьи » Мои статьи |
VPN: implementation of solutions and briefly about their advantages and disadvantages
In itself, the definition of VPN (virtual private network) is quite wide, and straight off it is difficult to say what can be considered VPN and what not. With a certain reserve VPN can be called the ancestor of the Internet ARPANET. Interestingly, almost all of the technology, and more often still, the protocols initially used for building distributed enterprise networks, has gradually become the main means of access to Network for standard users. Today, we meet with the variations VPN, are unprepared and not very knowledgeable in networking technologies, the user will be able to meet on the way.
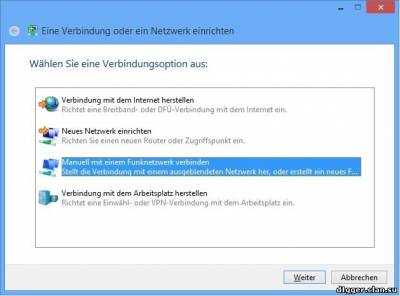
The first is to consider those that will help to protect yourself when using public Wi-Fi access and will allow to bypass the blocking of those or other resources. As a rule, accessible for private users, VPN services rely on the capabilities of the popular operating systems (OS) and can set up using the step by step instructions connection to them. In recent times the VPN services more streamlined this process — they hide the technical details and bring it to the level of "here to put money in it, from here download the program, click this button and enjoy life, not forgetting to fill the balance of personal account". However, in some cases, it may be useful to understand than some variations of VPN differ from others. PPTP (Point-to-Point Tunneling Protocol) appeared 20 years ago, and this is how its advantages and disadvantages. A definite plus of this Protocol is supported by virtually every OS, even very old. This provides some versatility and affordability. Besides, by modern standards it is very undemanding to computer resources.
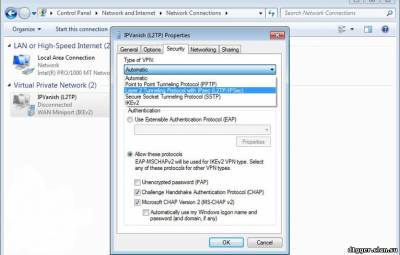
The reverse side of the coin — because of such a respectable age now he has low level of user protection. Seemed quite reliable in the mid-1990s, the methods of encryption by today's standards weak and combined with not the most successful architecture and a number of errors in the most popular implementation of the Protocol from Microsoft. In addition, the default encryption is generally not offered, and hacking the password on modern hardware possible in less than a day. However, in cases where the protection connection is not important or when there are no other options for VPN connections, it is better to use PPTP with encryption than without it. L2TP (Layer 2 Tunneling Protocol) is very similar to PPTP. These standards were developed and were adopted almost simultaneously, but L2TP is considered more efficient to build virtual networks, although a little more demanding of computational resources compared to PPTP. In fact it is used by ISPs and corporate users. Please note that by default, L2TP also offers encryption and is used simultaneously with other protocols — typically, this IPSec.
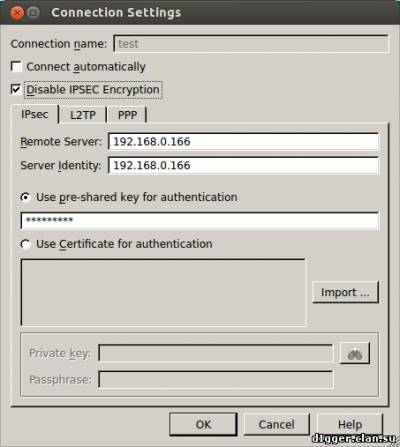
IPSec (Internet Protocol Security) is a set of protocols, standards and guidelines, specifically designed to create secure connections in the Network. The first results also appeared in the early 1990-ies, however, initially the goal was not "IPSec carve in granite," and regularly update it to meet the spirit of the time. It is easy to guess, for departments of any nature was conducted with these developments. Set IPSec consists of dozens of standards (and each of them has within itself more than one version) that describes the different stages of work with secure connections. He's really good and from the point of view of architecture and from the point of view of reliability of the used algorithms, and from the point of view of possibilities.
With all the advantages of IPSec is it does have disadvantages. First, for a beginner it is very complicated to set up, which, in turn, may reduce its level of protection in case something is wrong. Moreover, as noted, it is often used in conjunction with other technologies. Secondly, it is much more demanding of computational resources. Partly this disadvantage is compensated by the use of hardware acceleration for some variants of the AES encryption algorithm — it is available in modern versions of IPSec, although there are other versions of the algorithms. Such accelerators already exists in modern processors for both desktop and mobile devices, as well as Wi-Fi routers. Unfortunately, that well-thought theorists, in life practice translate, not always have a sufficient level of knowledge and understanding of the subject area. A study published in the October 2015 shows that up to 66% IPSec connections can be relatively easily hacked, and that the NSA may have suitable hardware for this hacking. The problem lies in the incorrect use of algorithms for initializing secure connections. And this applies not only IPSec, TLS and SSH, as well as TOR and OTR. That is, there is the potential for reading not only the VPN connections, and secure connections to some sites, email servers, instant messengers and so on. Yes, to implement this attack requires fairly long cooking and good computing resources, but in this case it is noteworthy that researchers have used cloud technologies Amazon and, apparently, spent the money, it is manageable and for individuals. After this preparation, the attack is reduced to minutes in the best case, or up to a month at worst. However, some experts are skeptical of this research — they claim that in reality, the percentage of vulnerable systems is not so great, though some aspects of research really should be taken very seriously, and developers are potentially vulnerable software (SW) has already released or plan updates and warned users. SSL (Secure Sockets Layer) and TLS (Transport Layer Security) VPN, as the name implies, are a class of solutions based on appropriate protocols SSL and TLS, sometimes supplemented by other methods of protection. Actually, SSL/TLS, each of you met in the first place on the web sites: the prefix https and a green padlock in the address bar say about the use of these protocols secure the connection. The first version of the Protocol appeared in the last century, but became actively used only in this. The prevalence of these protocols contributed to their detailed study and consistent identification of new vulnerabilities in architecture, and in specific implementations. SSL 3.0 was abolished in June 2015 actual current version is TLS 1.2, however, safe to assume its not much again depends on the implementation (see IPSec). In addition, both protocols were forced to bear the heavy burden of backward compatibility.
Plus SSL/TLS VPN is that due to the wide application of these protocols on the Internet, they freely ignored by almost all public networks. Minus — not too high performance in practice and the difficulty in setting up, as well as the need to install additional software. Popular implementations of SSL/TLS VPNs are OpenVPN (SSL 3.0/TLS 1.2), and Microsoft SSTP (SSL 3.0). Actually SSTP is tied to the Windows platform. OpenVPN because of its openness, has a variety of implementations for all platforms and is currently considered to be the most secure option VPN. We have listed only the most popular with private users types of VPN. However, during the years of development of this technology she had countless variations. As ordinary user I suggest to use, if at all possible, only OpenVPN because of its openness, reliability and security. However, for him and for other types of VPN there are still some tricky nuances of technical and legal nature, which we will discuss next time.
| |
| Просмотров: 974 | | |
| Всего комментариев: 0 | |