| Главная » Статьи » Мои статьи |
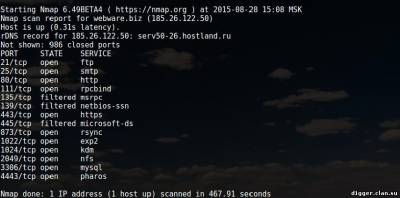
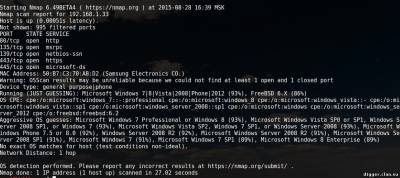
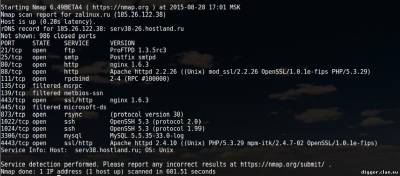
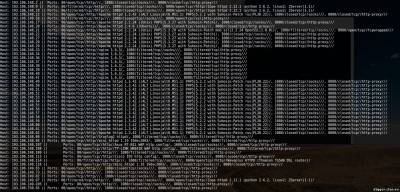
Nmap is a free, open source utility for network exploration and auditing security. It is widely used in the community of Linux users because it is easy to use, but at the same time very powerful. The principle of operation of Nmap, simply put, involves sending packets of data at the specified target (by IP), and in interpreting the returned packets to determine which ports are open/closed, what services are running on the scanned system is installed and enabled firewalls or filters and, finally, what operating system is running. These features allow you to collect a lot of valuable information. Let's look at some of these opportunities. Also typical of such articles of examples of teams that will provide guidance on how to use collected during the scanning data. For Kali Linux users, special actions are required because the tool exists and already installed with the system. For other systems, you will have to perform some steps. So for example: Install Nmap on CentOS Install Nmap in Debian To install Nmap in Ubuntu Now you can run the utility by typing in the terminal “nmap”. The list of options can be viewed on command: || nmap --help To show some of the capabilities of nmap, prepared a few examples. The main goal is that you caught the essence and the features of the program. You will then be able to modify the commands to fit your own needs. Please note that the program nmap requires root privileges for some of its functions. In Kali Linux it is not necessary, but all other systems run the command with sudo. In the examples I'll use sudo in Kali team look, but drop sudo. Collect information about open ports on the server, running services and versions of software This simple command can be used to check whether the website. Pay attention to the open ports. || sudo nmap -sS [IP address] or [address of website] The next option will instruct nmap to try to guess which operating system is running on the target system. If all ports are filtered, this team will be the best option, but the results cannot be regarded as reliable is guaranteed. Note interest — they indicate the probability of guessing. || sudo nmap -O --osscan-guess [IP address] or [address of website] Now, with the help of the team, we will try to figure out what service is running on the target system. Please note that there is a column VERSION — it contains the version of the software. || sudo nmap-sV [IP address] or [address of website] Also, you can use a string 193.106.148-153.1-255. It means to scan a subnet with 193.106.148.* on 193.106.153.*, and in each of these subnets can be scanned addresses *.*.*1 *.*.*255, i.e. it 193.106.148.1-255, 193.106.149.1-255, 193.106.150.1-255 etc. Searching for routers, web servers, web cameras At the routers, web servers, web cameras are usually open ports 80, 8080 and 1080. To scan these ports and output only the address to which something is open, enter the following command || nmap -sS-sV -vv-n -Pn-T5 193.106.148-153.1-255 -p80,8080,1080 -oG - | grep 'open' To scan FTP generally uses port 21, use the previous command, changing only the scanned port. || nmap -sS-sV -vv-n -Pn-T5 193.106.148-153.1-255 -p21 -oG - | grep 'open' If you are testing the penetration of a specific computer/server, then check all ports — from first to last (65535). If the range of the test network is small, we can set test all ports with filtering according to (ftp | grep 'ftp'), (ssh | grep 'ssh'), etc. for Example: || nmap -sS-sV -vv-n -Pn-T5 193.106.148.1-255 -p1-65535 -oG - | grep 'ftp' So, in General terms, in several examples, we showed you what is NMAP and how it works
| |
| Просмотров: 1164 | | |
| Всего комментариев: 0 | |